March 2025 Newsletter
Small and midsize businesses (SMBs) are increasingly becoming prime targets for cyberattacks. Unlike large enterprises with dedicated IT security teams, SMBs often operate with limited cybersecurity resources, making them vulnerable to breaches that can result in financial losses, reputational damage, and regulatory penalties. This is particularly true for businesses in Western New York, including Buffalo, NY, where many SMBs rely on digital technology but may not have the necessary protections in place.
Understanding the most common cybersecurity risks can help SMBs take proactive steps to protect their businesses. Here are the top cybersecurity breaches SMBs face and how to mitigate them.
Why You Should Never Reuse a Password
.png?width=275&height=275&name=Why%20You%20Should%20Never%20Reuse%20a%20Password%20(1).png) Every account needs a unique password. Reusing passwords is like having one key for your house, car, and office—if a thief gets it, they have access to everything.
Every account needs a unique password. Reusing passwords is like having one key for your house, car, and office—if a thief gets it, they have access to everything.
Data breaches happen. If a website you use gets hacked, your reused password could be exposed—leaving all your other accounts vulnerable.
Cybercriminals use credential stuffing. Hackers take stolen passwords and try them on other sites, just like a master key opening multiple locks.
Use a password manager. A password manager acts like a secure vault, generating and storing strong, unique passwords for each of your accounts.
Enable multi-factor authentication. Adding an extra verification step is like needing both a key and a code to enter a secure building.
Change compromised passwords immediately. If a password is leaked in a breach, update it right away—think of it as replacing a broken lock before someone walks in.
By using unique passwords for every account, you can keep your personal and financial information safe from cybercriminals!
Catch of the Month: eBay Receipt Email Scams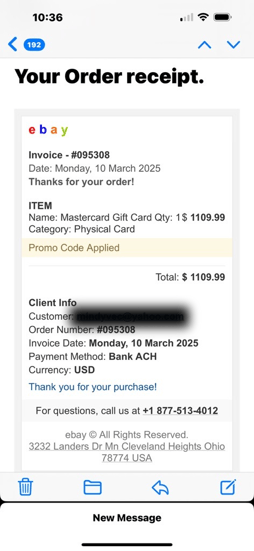
Scammers are getting more sophisticated, and the latest scheme involves fake eBay receipt emails. These fraudulent messages claim you've made a purchase and provide a bogus customer service number to dispute the charge. The goal? To trick you into calling and giving away personal or financial information.
How to Defend Yourself:
- Check the Sender – Look closely at the email address. Scammers often use slight variations of legitimate domains.
- Verify the Details – Legitimate eBay receipts match your account history. Log in directly at eBay.com instead of clicking email links.
- Look for Red Flags – Scammers may space out “eBay” oddly or use different fonts to bypass spam filters. Watch for typos, urgent language, or unfamiliar phone numbers.
- Never Call Unverified Numbers – Always use the official contact details found on eBay’s website, not the ones listed in the email.
By staying cautious and verifying before acting, you can avoid falling for phishing scams that aim to steal your information.
Get the Recording!
Live Training for Leaders: How to Use Copilot in Teams
Boost productivity with Microsoft Copilot by simplifying meetings, streamlining chats, automating tasks, and enhancing collaboration with AI-powered efficiency.
First Line of Defense Against AI Attacks
Learn to identify critical AI attack vectors, like adversarial attacks and data poisoning, and use tools like anomaly detection to enhance cybersecurity. Train your team as the first line of defense to mitigate AI security risks effectively.
How to Implement AI Securely in Your Business
Master the strategic deployment of AI tools like ChatGPT and Copilot across your team to enhance business processes. Learn to use the right prompts for optimal results and implement key strategies to securely integrate AI.






